Eleven Ransomware Prevention & Protection Methods. Cybercriminals increasingly rely on ransomware to carry out their campaigns of destruction on organizations globally with no appearance of stopping anytime soon. Here’s what to know about how to prevent ransomware and protect your data against attacks when they occur
It’s no secret that cybercriminals love using ransomware. They can use this malicious software to gain access to organizations’ data and lock them out of their own systems and offer a key in exchange for a massive payment. In some cases, attackers will even take things a step further, extracting the data so they can use it to commit additional crimes or publish it online to rub the proverbial salt in your wound. This is where implementing ransomware prevention and protection methods for your organization ASAP is crucial.
Needless to say, knowing how to prevent ransomware is crucial for every modern business. It’s important not just from a reputational standpoint but also from a compliance perspective. This article explores how to prevent ransomware from affecting you in the first place and what you can do as far as ransomware protection goes when you’re facing an attack.
11 Steps for Implementing Ransomware Prevention & Protection Within Your Organization
Now, we’re not here to just cover the latest ransomware attack news or the latest ransomware statistics. Instead, our goal here is to help prepare you by providing you with the right information to form a strong ransomware prevention strategy. That’s what this article is going to focus on. With this in mind, here are 11 ransomware prevention and protection measures you can implement within your organization.
1. Secure Your Network Perimeter with Security Tools and Processes
Implementing strong network security is one of the most important things you can do to secure your business. Your network is the connection between all of your servers, applications, and endpoint devices. If that becomes compromised, you’re in for a world of pain that comes in the form of noncompliance issues, penalties, and reputational damages.
Now comes the question of how to secure your network for greater ransomware prevention and protection capabilities. There are multiple ways to do this:
- Utilize network and endpoint security tools like firewalls and antivirus and antimalware software
- Monitor your network’s event logs for unusual access and activity
- Perform regularly risks analysis, security audits, and penetration testing
- Use encryption to secure your data both while it’s at rest and in transit
- Keep sensitive data and critical infrastructure on its own internal network (i.e., separate from a guest network)
- Use WPA2 as a minimum for Wi-Fi networks (and use a strong passphrase to secure it) and disable wireless protect setup (WPS)
- Require users to connect via virtual private networks (VPNs)
- Implement strong password security measures
- Restrict access to only authorized users through identity and access management measures
- Use strong authentication measures (like PKI-based certificate authentication)
- Train your employees on how to securely access and use your network (and connected resources)
- Train your IT security employees to know how to prevent and stop ransomware attacks
- Create documentation that outlines your processes and procedures for network security operations, management, and maintenance.
2. Keep Your Systems Up to Date Through Regular Patching (or Use Automation)
Regularly patching your devices is an overlooked aspect of cyber security. If you’re manually rolling out updates, this important activity can be a bit tedious. And we get it — on one hand, patching is a process that’s time consuming, monotonous, and takes you away from other critical tasks that require your attention. But, on the other hand, not applying patches leaves your applications, devices, and data at risk of attack by cybercriminals.
This is where automation can help. Implementing automatic updates and patching makes it so you no longer have to drop everything else you’re doing to handle this unexciting task. However, use this option judiciously; in some cases, it’s best to implement some updates manually to avoid issues like what we saw recently with Microsoft’s Windows 10 updates last year.
3. Implement Access Controls to Limit Access to Sensitive Data and Systems
Setting up strict access management processes can help mitigate ransomware risks by restricting access to your most sensitive systems and infrastructure. This way, only select users have access (reminder: everyone doesn’t need access to everything!)
You can do this by:
- Implementing access controls and setting user permissions across the board using Active Directory
- Following digital identity and access management best practices
- Following PKI management and SSH key management best practices
- Using secure authentication methods
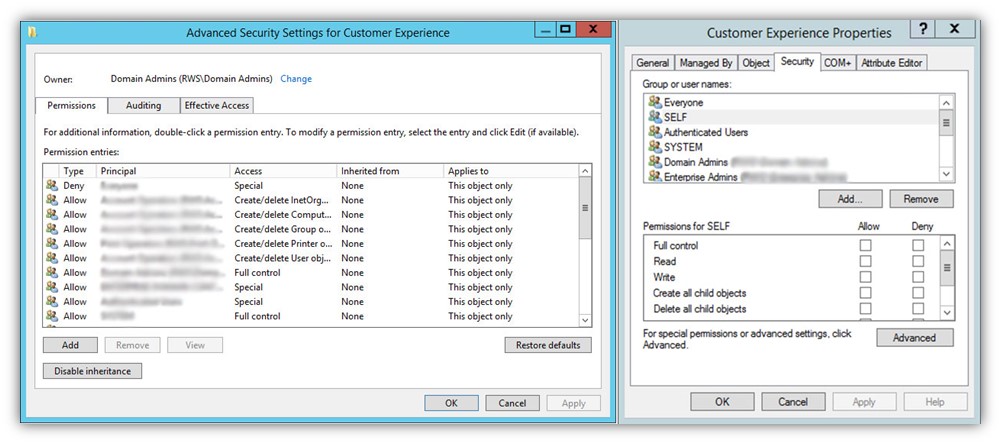
If an attacker doesn’t have direct access to your systems, then they’ll have to rely on other methods to access your critical resources. In this case, they’ll typically take advantage of other security gaps that, ideally, you’ll have fixed by implementing the other ransomware prevention and protection steps outlined in this article.
4. Lock Down and Monitor Your Remote Desktop Protocol (RDP)
Since the start of the COVID-19 pandemic, we’ve seen a significant increase in the remote workforce. This is great in many ways, but remote access also poses a security threat to an organization if not implemented well. In particular, this risk can be seen when it comes to the use of remote desktop protocol.
RDP is a useful tool for IT admins who need to access employees’ devices remotely to troubleshoot issues or carry out other essential tasks. But things can go downhill quickly if an unauthorized user gains access to this tool. This is why it’s crucial that you secure and monitor this form of access. You often can do this using firewalls and third-party monitoring tools that monitor usage, users, or both. Furthermore, you can set firewall rules that:
- Restrict access or connections from specific devices and/or users
- Set it so only secure connections are allowed (or block connections altogether)
In general, a good idea if you’re going to use RDP within your organization is to require users to turn on a VPN prior to starting a remote desktop connection.
5. Secure Your IoT Devices Against Unauthorized Access
Unfortunately, many Internet of Things (IoT) devices are known for having unmitigated vulnerabilities. When exploited, these vulnerabilities can give attackers access to the devices’ data and your larger network as a whole. This is why having strong IoT security is imperative for any business that use smart devices.
While it makes for an exciting plotline in movies and TV shows, spending days, weeks or hours trying to hack through firewalls typically isn’t how cybercriminals gain access to companies’ systems. It’s too cumbersome, time-consuming, and requires more effort than they’d want to devote to the task. Instead, they typically use the path of least resistance by exploiting known vulnerabilities. And considering that IoT devices are often chock full of different security vulnerabilities, they make perfect targets for low-fruit-grabbing cybercriminals.
Check out our other article to learn more about how to secure your IoT devices within your enterprise.
6. Have Business Continuity and Emergency Response Plans In Place (And Test Them!)
The worst time to try to figure out what you should do when facing a ransomware attack is when you’re in the middle of one. Unfortunately, many organizations either don’t bother to create these plans or if they do, they fail to test them ahead of time to ensure that they work.
Testing your data backups is imperative; after all, why bother having backups in the first place if you don’t bother checking to ensure they work?
Be sure to have data backups (which we’ll talk about later in this article) and regularly test their restoration capabilities. This way, you’ll know whether your backup work and will meet your needs in a real-world situation.
7. Train Employees to Recognize Phishing Scams and Websites
This isn’t the first time we’ve talked about cybersecurity training for employees, nor is it going to be the last. The truth is that employees represent a big risk surface for organizations. Whether it’s intentionally malicious actions, earnest mistakes, or pure negligence, your employees’ actions can make or break your organization’s security defenses. This is why it’s so crucial that they know how to recognize scams and what they should do when they receive suspicious messages.
Cyber security training should encompass a multitude of concerns and topics:
- Common elements of phishing scams and websites
- Real-world examples of what phishing emails and sites (so they know what to look out for)
- What to do when they receive phishing messages and phone calls
- Who to report suspicious behaviors and messages to and what the processes are
We’ve put together a list of resources that you might find particularly helpful when educating and training your employees
- 10 Types of Phishing Attacks and Phishing Scams
- 12 Days of Phish-mas: A Festive Look at Phishing Examples
- What Is Smishing? Definition, Examples & Protection Tips
- 5 Ways to Determine If a Website Is Fake, Fraudulent, or a Scam
- How to Spot & Protect Against Business Email Compromise (BEC) Attacks
- What to Do with Suspicious Emails: How to Report Scam Email
8. Implement DMARC to Prevent Email Domain Impersonations
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) recommends organizations use domain message authentication, reporting and conformance (DMARC) as part of their ransomware prevention strategy. The idea here is that DMARC, which builds upon both the sender policy framework (SPF) and domainkeys identified mail (DKIM) protocols, prevents unauthorized users from sending emails from your domain.
If you enable DMARC, you’re basically creating DNS records that restrict which servers are authorized to send emails on behalf of your domain. If someone tries to impersonate an executive within your company in an email to Derek on your HR team, the email will be rejected automatically because the attacker won’t be sending the message from an authorized mail server.
9. Get Cyber Liability Insurance to Protect Your Organization
Cyber insurance is a great tool for every business to have in their arsenal. While it doesn’t stop you from getting attacked by ransomware in the first place, it does offer at least some protection when an event happens. For example, some types of cyber liability insurance cover ransomware costs and system recovery costs due to these attacks and other issues.
Check out this article that talks about five situations in which cyber liability insurance would be helpful.
10. Keep Multiple Copies of Current Backups Readily Available
A good rule of thumb is to maintain multiple current, secure copies of your data backups. This typically involves storing copies on-prem, at a second geographic location, and maybe even in a cloud environment. Of course, having data backups doesn’t stop you from getting hit (i.e., it’s not a ransomware prevention method). But this way when something goes wrong, you have your backups to fall back on so you’re not starting over from scratch.
Of course, data backups aren’t going to offer the restoration protection you need in all ransomware cases. Over the last two or so years, we’ve seen an increase in the use of ransomware that targets data backups. The goal here is for attackers to gain access to cloud backups so they can either encrypt them or destroy them outright, thereby preventing you from restoring your data from backups. This brings us to our last point….
11. Store Your Most Sensitive Data and Backups in Offline Servers
Having air-gapped data backups or storage servers can help in this situation. An air-gapped computer is a standalone device that isn’t connected to any networks, meaning that even if your network gets compromised, this offline data won’t be affected. Basically, it’s an isolated resource that can be used to house your most sensitive data without fear of an attacker gaining access through traditional means.
By keeping at least one copy of your data in this isolated environment, it means that you’ll at least have some data that bad guys can’t get their hands on without physically gaining access to the tapes or devices that it’s stored on. Basically, in most cases, they’d have to physically gain access to your secure server room or wherever it is that you have the data stored.
It’s important to note that there is still a small security risk even when using an air-gapped system. An attacker could potentially use an exploit that converts your air-gapped device’s RAM card into a Wi-Fi signal emitter. But the good news here is that there are steps you can take to mitigate these risks. (Check out the linked article above for more info on that.)
Why Ransomware Prevention Matters (And Why You Need Leadership Buy-In For Ransomware Protection Initiatives)
The latest Internet Crime Report (2021) from the FBI Internet Crime Complaint Center shows that ransomware was one of the top cyber crime complaints received in 2021. There were 3,729 ransomware-related complaints with adjusted losses surpassing $49 million. (Note: this number represents only reported incidents; it doesn’t count any ransomware events that went unreported.) This is an increase of 1,255 reported incidents and more than $20 million in additional adjusted losses than the IC3 shared in their 2020 report.
What’s particularly disturbing are the stats regarding the critical infrastructure targeted by ransomware attackers. For example, 649 of the ransomware-related complaints the IC3 received in 2021 came from organizations that fall within the critical infrastructure sectors. The highest-reporting sectors were healthcare and public health (148) followed by financial services (89) and information technology (74).
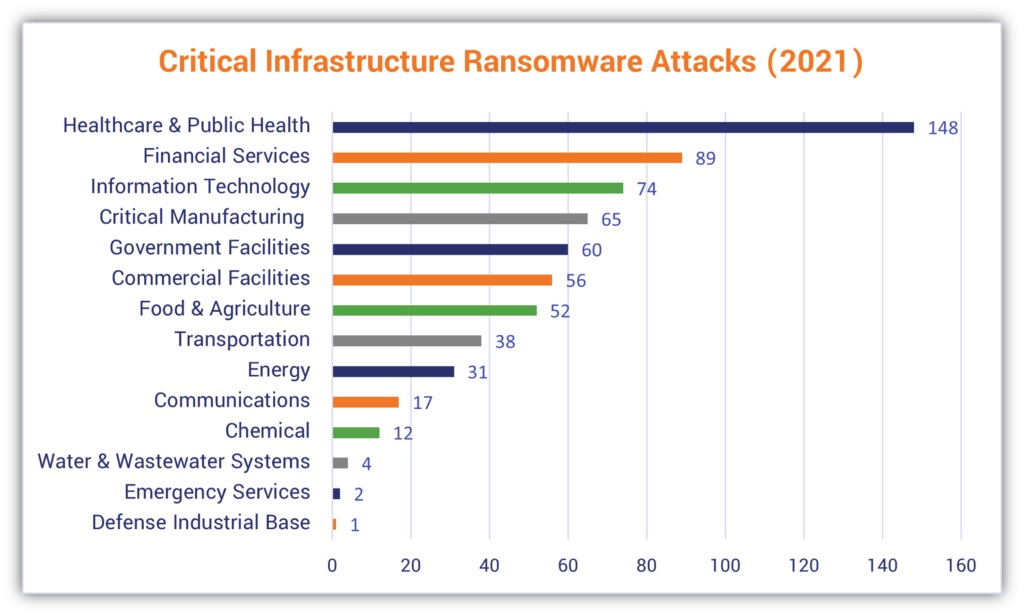
One of the scariest types of targeting involves energy, agriculture, and water systems. We reported on one such attack last year when a hacker breached a water treatment plant here in Florida.
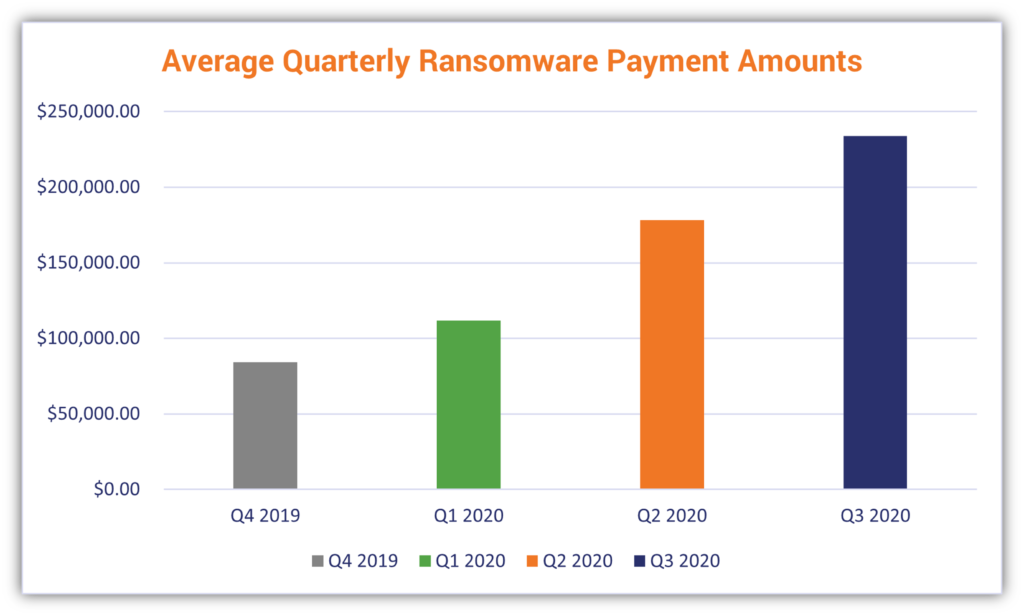
Average Ransomware Payouts in 2020
In their 2021 Threat Report, Sophos indicates that the average ransomware payment jumped from $84,116.00 in Q4 2019 to $244,817.30 in Q3 2020:
But how many organizations actually choose to pay ransomware demands? That answer varies from one source to the next, as many organizations don’t bother reporting ransomware payments. For example, data from International Data Corporation (IDC) shows that 87% of organizations that experience a ransomware attack choose to pay the ransom.
But does making these payments actually benefit you? Not necessarily. Sophos’s report The State of Ransomware 2021 shows that organizations that chose to pay attackers’ ransomware demands only got back a little less than two-thirds (65%) of their encrypted data. In nearly 30% of their observed cases, less than half of the affected organizations’ files were restored. So, paying an attacker likely won’t benefit you in terms either ransomware prevention or protection.
But what about the costs of dealing with ransomware attacks (both direct and indirect)? In the same 2021 ransomware report, Sophos gave the price tag of a cool $1.85 million in 2021. This is more than double the amount reported by organizations in 2020.
When Bad Guys View Ransomware On Its Own As No Longer Enough…
Just when you thought ransomware alone was bad enough to deal with — ransomware gangs have been increasingly integrating DDoS attacks into their strategies as well. NETSCOUT’s 2H 2021 Threat Intelligence Report shows that ransomware attacks overall have jumped 232% since 2019. But what makes this situation worse is that attackers are now taking the two-pronged attack involving ransomware and either data theft or leakage and lighting a fire under it by adding distributed denial of service (DDoS) to the mix.
NETSCOUT’s report shows that ransomware attacks involving DDoS have been on the rise and that VoIP service providers in North America, Europe, and the U.K. were targeted by such three-pronged attacks in 2021. One unnamed VoIP company in particular reported revenue losses of up to $12 million due to these types of DDoS extortion attacks.
Final Thoughts on How to Effectively Implement Ransomware Protection and Prevention
As you’ve learned, there are ransomware prevention steps that your organization can take to prevent it from becoming the next ransomware victim. But in the event that you find yourself facing the unenviable situation of having your systems and data encrypted by an attacker, here are a few additional things you should (and should not) do as far as ransomware protection goes:
- Seek help from professional incident response professionals. This will help you mitigate vulnerabilities and prevent further damage.
- Report any ransomware-related incidents to law enforcement. You’ll want to report any ransomware-related incidents to the FBI or the Internet Crime Complaint Center (IC3), the Federal Trade Commission (FTC), or other law enforcement agencies in your geographic region.
- Don’t pay the ransom. The concern here is that paying ransom demands can encourage threat actors to attack you again, knowing you’ll pay out, and it also emboldens them to attack others. Lastly, even if you do choose to make the payment, it doesn’t mean you’ll get your data back (as we learned earlier from Sophos’s research data)
When it comes to ransomware payments, there have been some interesting developments that have occurred over the past few years:
- An FBI official warned the U.S. Senate Judiciary Committee against banning ransomware payments. The concern is that by making payment illegal, it’ll lead to further blackmail situations of organizations that do choose to pay attackers.
- U.S. Department of the Treasury warns that you can personally face civil penalties in some cases for making ransomware payments.
Of course, choosing whether to pay an attacker is a decision that every organization must make for itself as there are many variables to consider in this type of situation. This is why it’s best for organizations to have emergency response and business continuity plans in place ahead of time.